DKIM
I wrote last year about using “stunt” nameservers for customer subdomain authentication – i.e. dynamically generating all the authentication records needed in DNS for each customer as needed. For example, if you’re an ESP that has customers who can’t or won’t use their own domains and you still need to give them unique subdomains you can generate CNAME records to support white label DKIM authentication: selector ._domainkey. customerid .espcustomer.com CNAME selector .dkim.esp.com or generate white label DMARC with useful rua= reporting: _dmarc. customerid .espcustomer.com TXT “v=DMARC1 p=none rua=rua+ customerid @esp.com” Once you’ve set up these DNS records once they’ll work for all your customers, you just need to put the right domains in your DKIM signature and return path. I shared some demo code to explain the concept last year, but since then we’ve developed a robust, production-ready application to dynamically serve DNS in this way. It’s called
This article takes a look at DKIM Selectors in particular, and we explain: What DKIM Selectors are Where to find your own DKIM Selector Third-Party providers and DKIM Signing How does DKIM work? DKIM (DomainKeys Identified Mail) is an email authentication method that allows an email receiver to check that an email that claimed to come from a specific domain was indeed authorized by the owner of that domain and received without any unauthorized modification to its content during transit. This is achieved through the use of cryptographic authentication with the use of a cryptographic key pair—a private key and a public key. The Mechanics of DKIM Digital Signature Creation: When an email is sent, the originating email server generates a unique digital signature for the message. This signature is based on the content of the email itself, including headers and body, ensuring that any alteration of the email during
In February 2024, Google and Yahoo started implementing a series of gradual enforcements for organisations that send over 5000 emails daily, also defined as bulk email senders. These enforcements are especially relevant to Domain-based Message Authentication, Reporting & Conformance (DMARC). With this initiative, Google and Yahoo intend to reduce the overall amount of spam and spoofed content sent across the internet, especially focusing on the authentication of an organisation’s email infrastructure. This move, aimed at combating spam and improving email security, involves using Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and DMARC standards. This article covers the Google and Yahoo requirement specifications and focuses on the potential impacts on European businesses. In particular, it addresses the complications of implementing DMARC across the European email ecosystem and the necessary steps to comply with the enforcement. Impact on European Email Senders: A Closer Look Popular Email Providers in Europe Challenges of
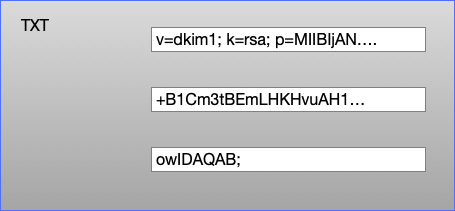
TXT Records DKIM public keys live in DNS TXT records. A DNS TXT record contains strings of text, and each string is limited to be no more than 255 characters long. Recommended practice for DKIM at the moment is to use 2048 bit keys (1024 bit keys aren’t insecure, but they’re looking a bit weak and 2048 is where folks have mostly decided to move to). But a 2048 bit DKIM key is going to be around 400 characters long. So how do we fit that into a TXT record? A TXT record can contain more than one string, so we can split the 400 character public key into two strings, put both of those strings in a single TXT record and the DKIM validator will join those two strings back together and use them to validate the email. A single TXT record containing three strings Editing your DNS Unfortunately
DomainKeys Identified Mail (DKIM) is an email security standard designed to help prevent email spoofing. It works by adding a “tamper-proof” seal to email messages, ensuring their authenticity and integrity. However, sometimes legitimate emails fail DKIM signature verification due to canonicalization issues, leading to email delivery problems. This article explains how to resolve these issues by adjusting DKIM canonicalization settings on your email gateway systems. Below is a representation of how DKIM works in an email infrastructure: Video: DKIM Overview Here’s a brief DKIM overview to help you understand its role in email authentication and DMARC. Understanding DKIM Canonicalization Canonicalization in DKIM refers to the method used to prepare an email’s header and body for signing. According to RFC 6376 Section 3.4, there are two canonicalization algorithms for header and body: simple and relaxed. The choice between these settings affects how strictly the email’s content must match the sending and
It’s time for another Webinar Rewind! Recently I presented (alongside Jesse Kennedy) a live webinar specifically meant to help AWeber users get up to speed on the new sender requirements brought to us by Yahoo and Google. With a focus on the specifics of what buttons to push, what text to paste into what field, even where and how to buy a domain — from start to finish, how to configure your email domain so that your AWeber email sends are fully in compliance with the new email authentication requirements. If you missed it, don’t fret! You can find the recording here and embedded below. We made sure to save time to take your questions, and did a bunch of live poking at email authentication and domain DNS settings, so you could see us push the buttons that you yourself need to push to get everything in place. As an
As you well know, Gmail and Yahoo Mail are now requiring that all senders start to publish a DMARC record, if they weren’t publishing one already. Hopefully you watched the webinar with LB Blair and myself (I’ll link to the recording here as soon as it is available) where we talk at length about DMARC and what you need to know to start to be able to “speak DMARC” as needed. But if you didn’t watch that? And don’t have the time to dive into making yourself a DMARC export? What’s the five minute version of all of this, how do you get up and running quickly without having to stop and worry about RFCs and options. “Just tell me what I need to know to get it done.” Okay, I got you. Here we go. Before you proceed with this, you need to ensure that you’ve implemented DKIM authentication for
The Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), Federal Bureau of Investigation (FBI), and Multi-State Information Sharing and Analysis Center (MS-ISAC) have released Phishing Guidance—Stopping the Attack Cycle at Phase One to provide guidance in the ever-waging battle against phishing exploits. The guidance is relevant to all organizations, though it may pose challenges for those with limited resources. To address this, the guide incorporates a section with customized suggestions tailored for small- and medium-sized businesses that may lack the resources for a dedicated IT staff to consistently combat phishing threats. For software manufacturers, the emphasis is on adopting secure-by-design and default strategies. The guidance encourages software companies to create and deliver software that is resistant to common phishing threats, ultimately enhancing the cybersecurity resilience of their customers. In the phishing mitigation guidance for all organizations, CISA, NSA, FBI, and MS-ISAC recommend organizations implement DMARC and other controls
Starting February, 2024, long established email authentication best practices will become a requirement. It’s as simple as that, folks. This news may be alarming to you for a variety of reasons; you may have previously interpreted these guidelines as being optional or didn’t understand the related technical complexities. Or maybe you trusted that your email service provider, or IT Department was taking care of this for you. Whichever camp you may be in, the responsibility is yours to ensure you are compliant and have the proper visibility to maintain that favorable status from that point forward. As abuse continues to mature, so must the controls that have been implemented to secure the email channel. We applaud Google and Yahoo for ushering this new reality in much of the same way that dmarcian has always taken a standards and best practices approach. Our mission has been to spread DMARC across the
As 2024 approaches, major players in the email industry, such as Gmail and Yahoo, are ushering in a pivotal shift that carries significant implications for email marketers and senders alike. Gmail’s New Email Requirements Gmail’s new email requirements are designed to bring a higher degree of security, transparency, and user-friendliness to the inbox. These requirements are specifically tailored for bulk senders — those who dispatch more than 5,000 messages to Gmail addresses daily. While this threshold may seem imposing, the impact of these changes is poised to benefit email marketers, recipients, and the email ecosystem as a whole. Concurrently, Yahoo is unveiling a parallel set of prerequisites. This collaborative initiative involving prominent industry leaders underscores a shared dedication to enhancing email communication, prioritizing security, user-friendliness, and freedom from spam. Significance for Email Marketers The significance of these changes cannot be understated. They signify a critical step towards a safer, more